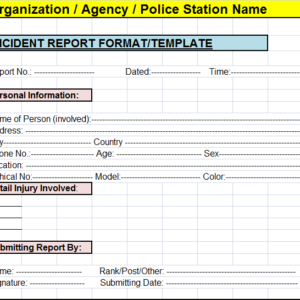
Ready-to-Use Templates for Security, Injury, Environmental and General Workplace Incidents. Below you'll find an incident response template that you can customize, an incident response plan for protecting privileged. Our collection comprises of various Free Report The template options are as follows: You may also see Blank Incident Report Templates. Review recent postmortems in meetings with the broader organization.
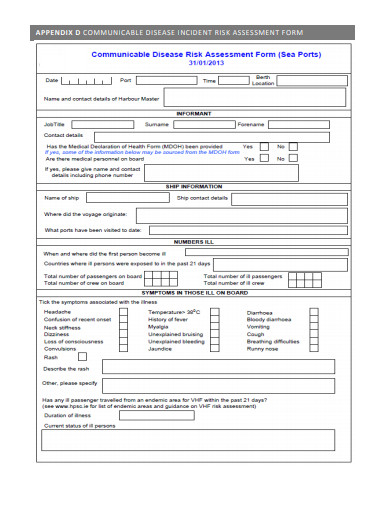
Many teams use a comprehensive template to collect consistent details during each postmortem review.
Create an example template to use in the Incident form. Communicate impact of incident and incident response actions (e.g., containment: "why is the file share down?"), which can be more intrusive/disruptive during ransomware incidents. Many teams use a comprehensive template to collect consistent details during each postmortem review.
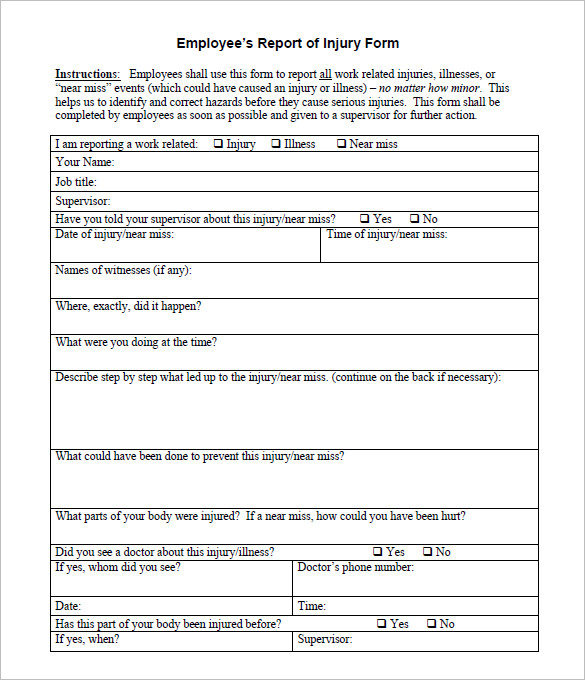
In this episode i wanted to look at how to write an incident report also referred to as a postmortem.

It is impossible to review all alerts, not to mention investigate and respond to all security incidents.

The VictorOps Post Incident Review Template to improve the DevOps on-call engineering experience and help turn incidents into actionable insights.
The purpose of this Computer Incident Response Plan (CIRP) is to provide the University with a plan that addresses the dynamics of a computer security incident. Prepared by: XXXXXXX School District Last Modied XXXXXXX. Download a Free Incident Report Template Pack. In this episode i wanted to look at how to write an incident report also referred to as a postmortem. Click here for an incident response demo.
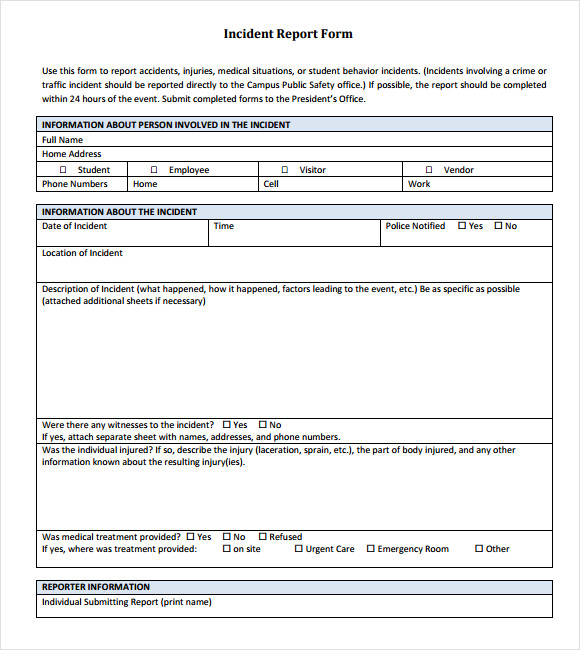
The VictorOps Post Incident Review Template to improve the DevOps on-call engineering experience and help turn incidents into actionable insights.
A well-conceived incident response plan helps deal with incidents effectively. These reviews are opportunities to improve both our IT infrastructure and. Use our incident response template to create a robust incident response plan. Communicate impact of incident and incident response actions (e.g., containment: "why is the file share down?"), which can be more intrusive/disruptive during ransomware incidents.